Install APC Demo App
Please note that the demo app needs Android Protected Confirmation (APC) support. Currently only Pixel 3 and above devices support APC.
Click the following icon to install the app from the Google Play Store:

The source code will be published on GitHub soon. That's the way if you want to analyze the code and or compile the app yourself.
Have fun.
Usage
The use of the app should be self-explanatory. If not - complain to me. The following Android devices are known to support the optional Android feature Android Protected Confirmation (APC) (These are the successfully tested devices so far, probably there are more):
- Pixel 3 XL
- Pixel 4a
- Pixel 5
- Pixel 6
- Pixel 6a
- Pixel 6 Pro
- Pixel 7
- Pixel 7 Pro
Key Generation
First you need a APC key pair. The grayed-out seal indicates that no key pair exists yet. Clicking on the seal or on the APC button will guide you to the key generation mask:
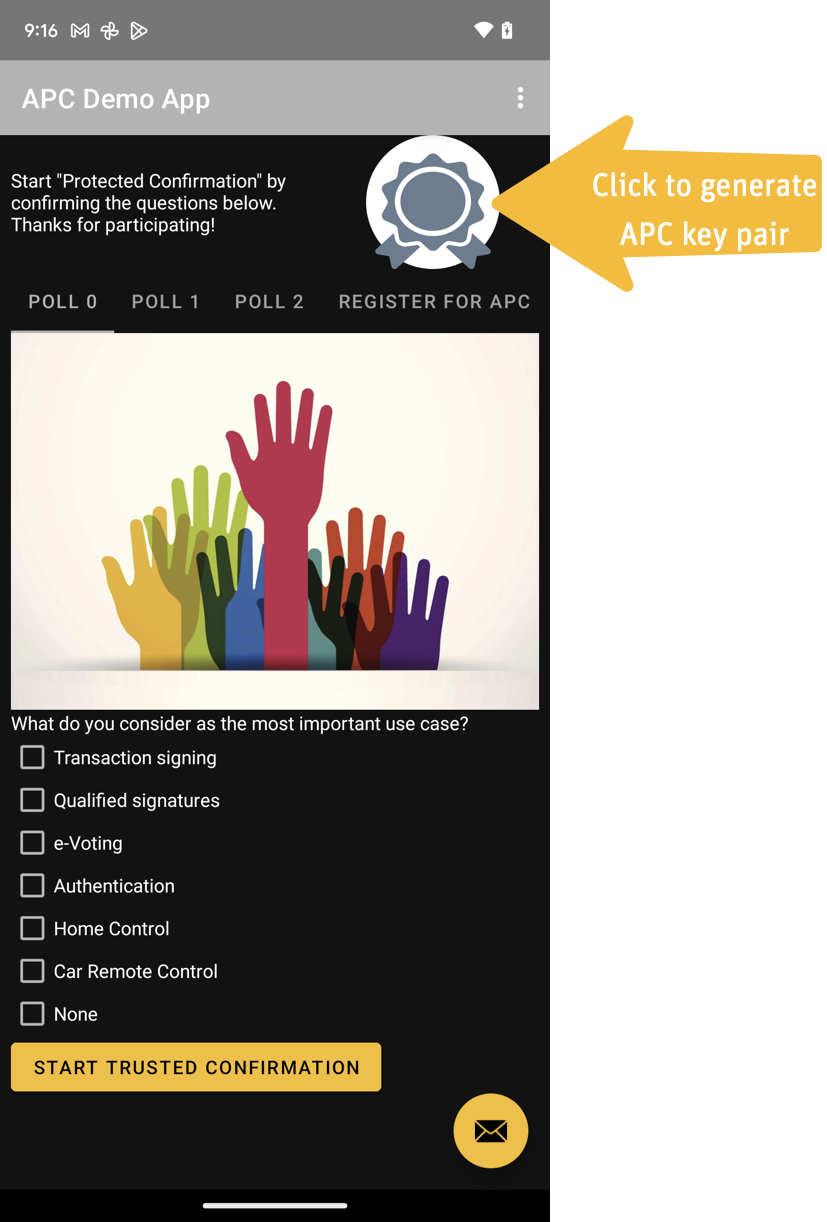
Android smart phones such as the Pixel devices have multiple hardware stores to choose from:
- Secure Element (SE): This is the most secure way to protect your keys. The SE is a certified HSM. On Pixel 3+ devices the Titan M cryptoprocessor serves as SE.
- Trusted Execution Environment (TEE): This is still a hardware key store. However, in general it is not a dedicated cryptoprocessor and it has no certification.
Please note that only the following key types are supported on the Titan M crypto-processor:
- EC: secp256r1
- RSA: up to 2048 bit keys
Inspect attested Key Pair
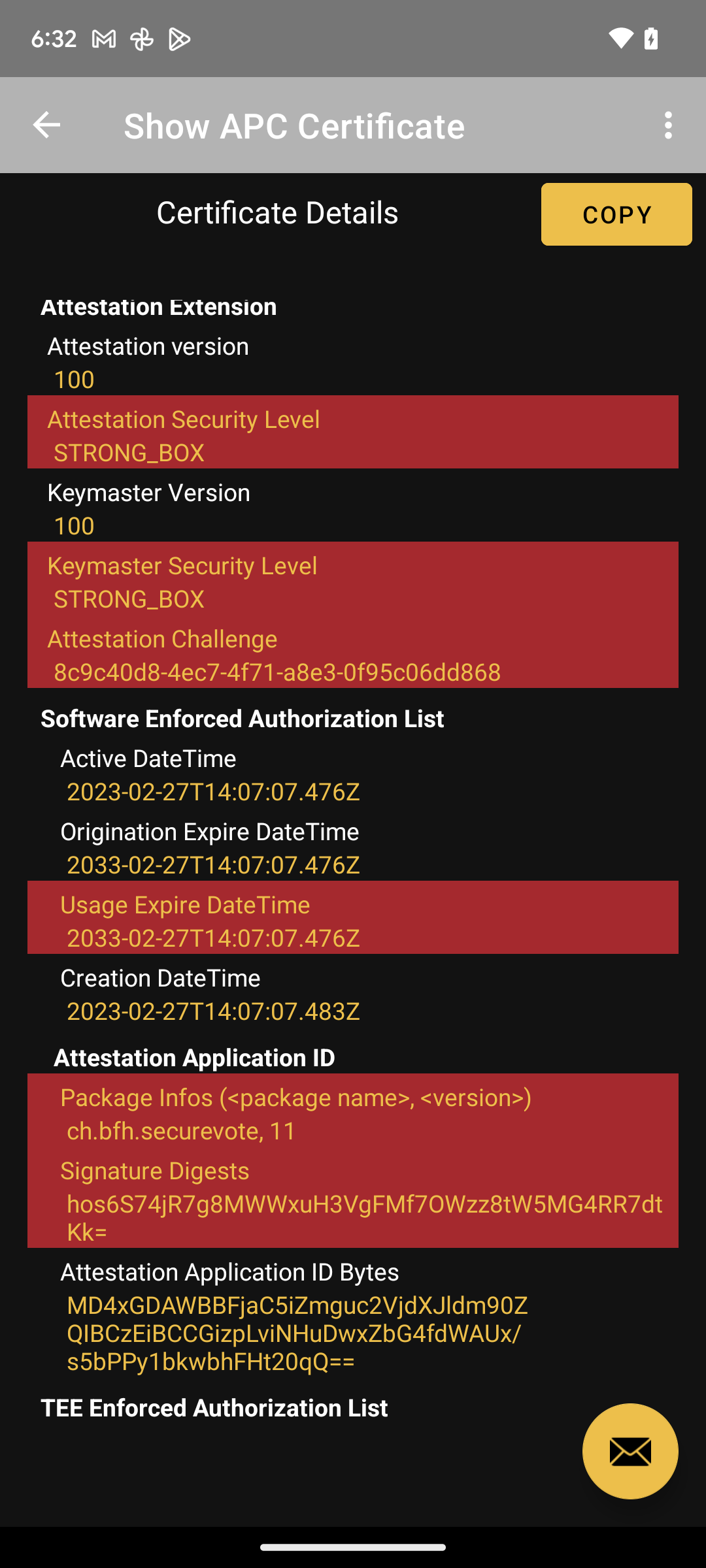
Clicking on the seal will display the details of attested APC certificate:
The certificate allows to determine the context where the key pair was generated and the context how the key pair can be used:
- Type of authentication
- Environment requirements such as
- Can only be used for Trusted Confirmation
- Can only be used on Unlocked Device
- ...
- Environment of key generation such as
- Device state such as locked, unlocked
- Boot state
- Model
- Device
- OS Level
- Patch Level
- Boot Patch Level
- OS Level
- ...
- Package info of the app that generated the key pair
- Generation date time
- Validity date time range
- Key purpose such as Encrypt, Decrypt, Sign, Verify, Wrap Key, Derive Key
- ...
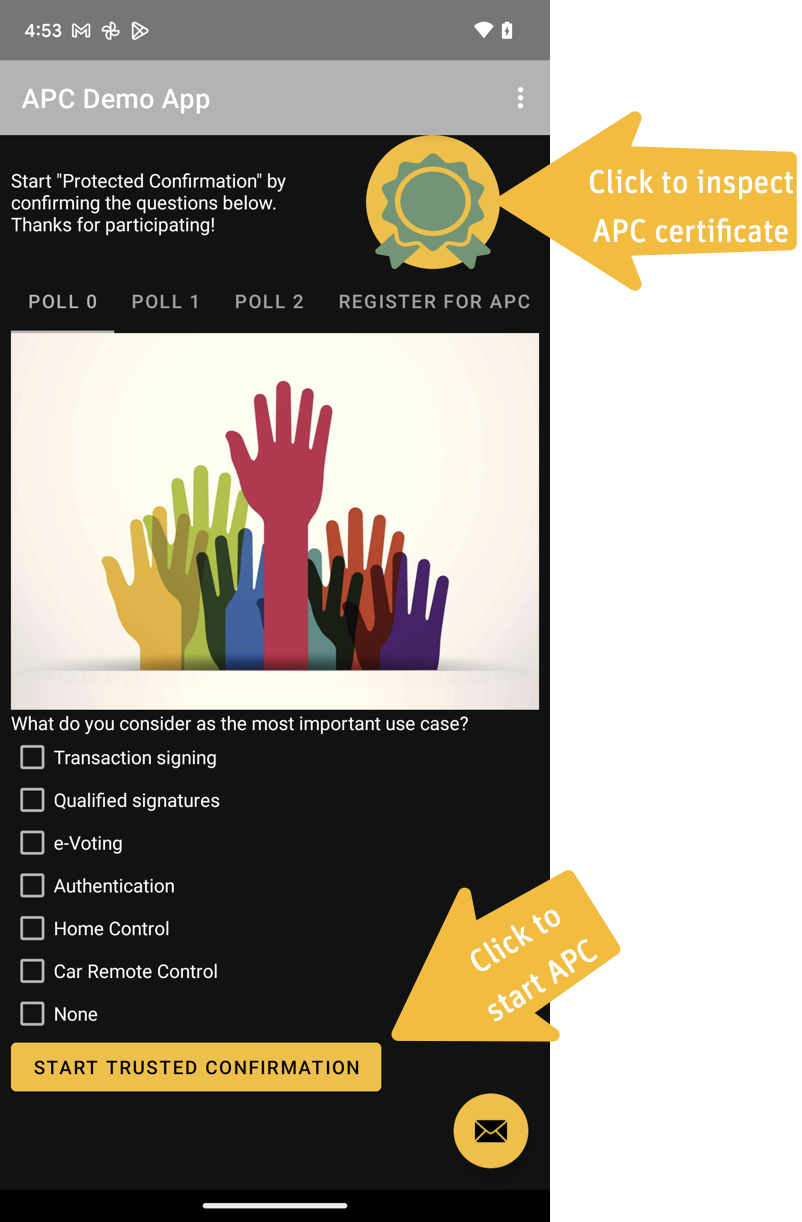
Trusted Confirmation
APC is started by clicking the button Start Trusted Confirmation. The screen which pops up is a Trusted User Interface outside the control of the Rich Execution Environment of the OS.
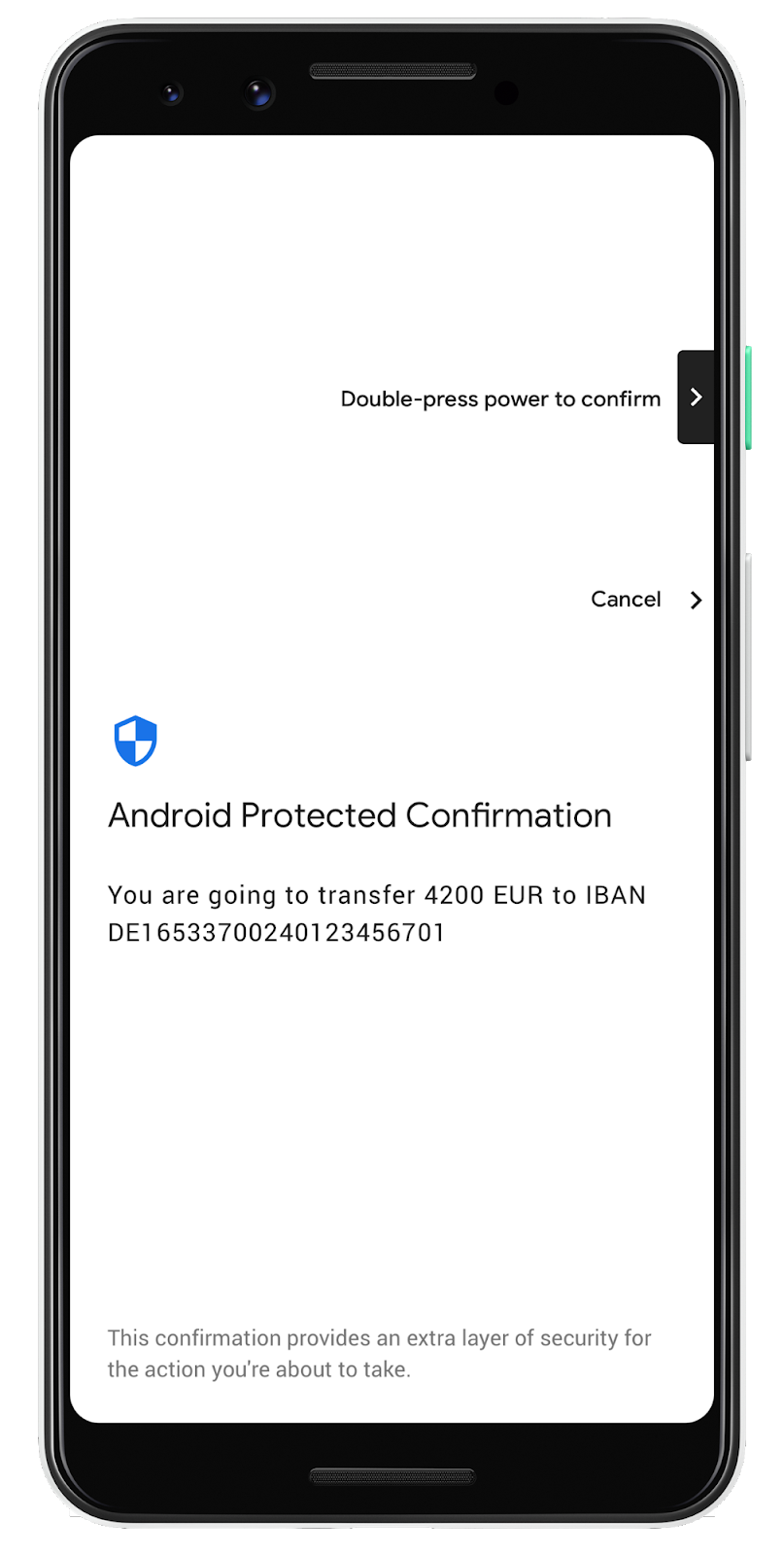
Actually the APC call takes 2 parameters:
setPromptText
This method takes the text string displayed on the Trusted UI. That is the message to be confirmed by the user. The message must not be longer than 420 chars and must not exceed 9 lines.setExtraData
This method takes a byte array. These extra bytes allow to make sure that the message belongs to a new request and hasn't been processed before. This step protects against replay attacks.
Signed Confirmed Message
A successful confirmation generates a P7M encoded signed message, containing the full attestation chain. The P7M signed message can be inspected by clicking on Analyze Signature.
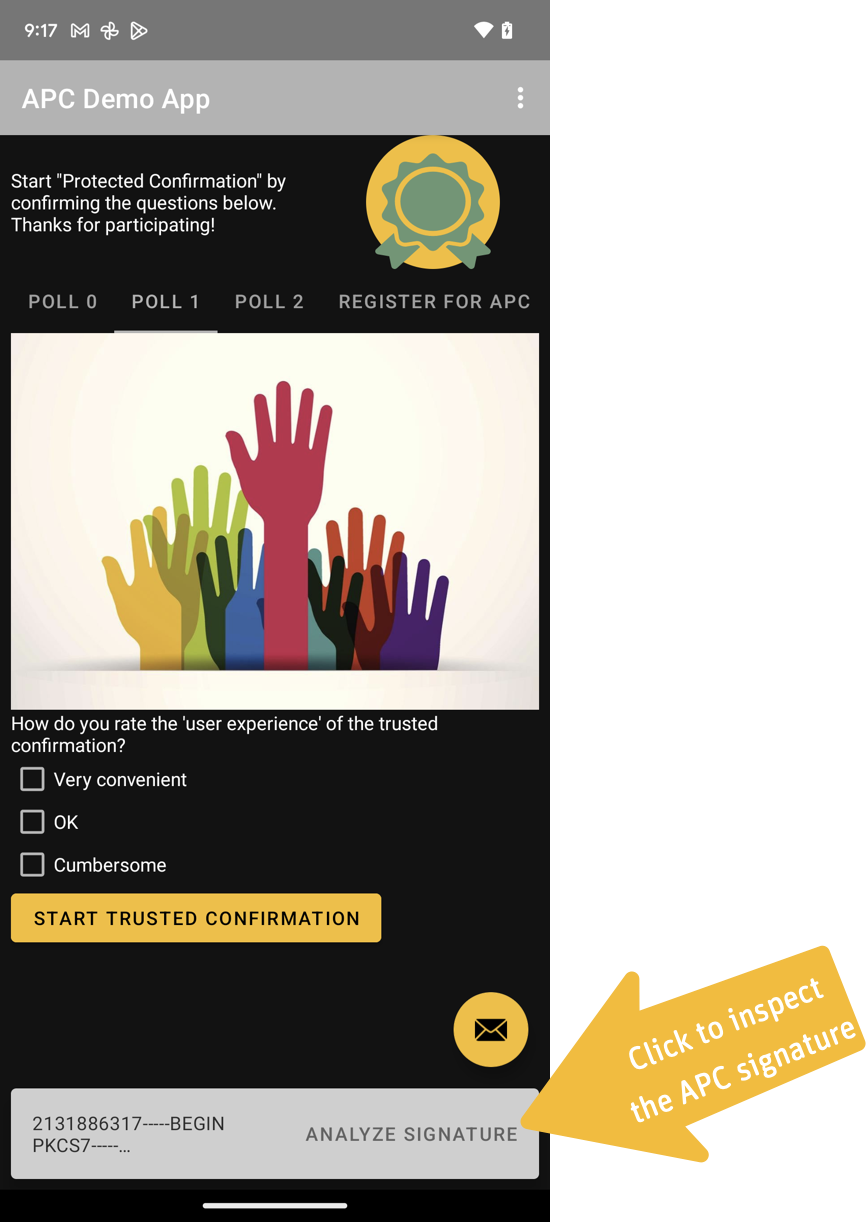
The message will contain:
- The signed message confirmed by the user on the Trusted UI.
- The APC signing certificate. This certificate contains the attestation extensions defining context of generation, key usage and context of usage of the certificate.
- One or multiple intermediate certificates belonging to one of the trust stores of you mobile device. The intermediate key pair signs all key pairs generated on the device's key store. This ensures that the APC key pairs are generated on the key store and under the conditions as specified in the attestation extensions. These key pairs are generated and signed at the factory.
- The Manufacturer Root Certificate. This certificate is injected into the device's hardware-backed keystore at the factory. The key pair is used to sign the certificates of the key stores. Google has currently 4 valid root certificates worldwide.




